Recently I wanted to connect to a machine with my admin user but then I realized that this user had been locked out in Active Directory. The counter for bad passwords is relatively high and gets resetted frequently, like every 15 minutes. So what could cause this issue? There must be some wrong configuration. I started to investigate. Analyze User Lockout AD
Imagine a setup with multiple Domain Controllers. Firstly, you have to find out which DC causes the lockout. Microsoft offers an amazing toolbox called “Account Lockout and Management Tools”. They are available at the following URL:
https://www.microsoft.com/en-us/download/details.aspx?id=18465
LockoutStatus.exe
Simply start the LockoutStatus.exe with a Domain Admin or at least with sufficient permissions and enter the target admin user who had been locked out. The tool will determine all Domain Controllers and show you a list of “Last Bad Password”, “Bad Password Counter” , “Last Password Change Date” and so on. Now you should know the involved Domain Controller.
Check Event Log on DC to analyze User Lockout AD
Secondly, you will connect via Remote Desktop Connection (RDP) to the mentioned Domain Controller and start the Event Viewer there. Navigate to System -> Security:
Now filter the current log for the event ID: 4625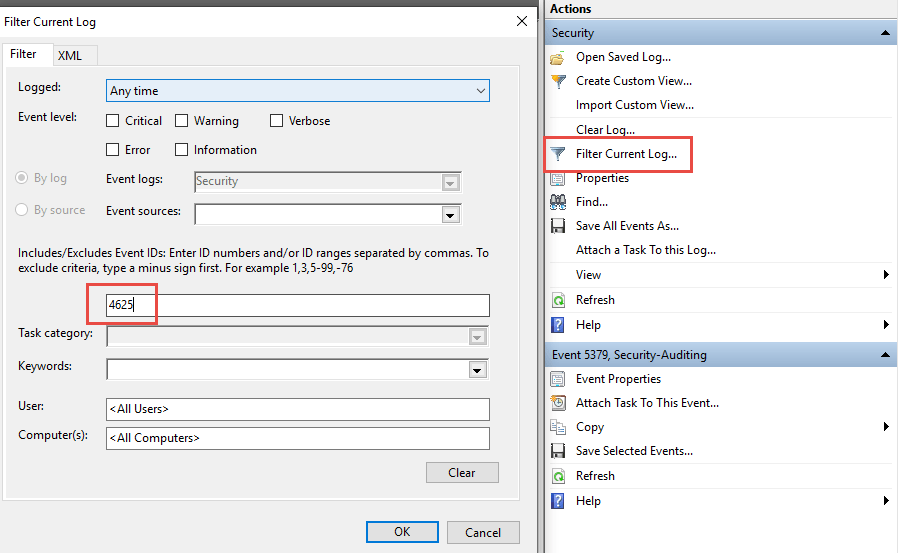
After that you should be able to see the corresponding log entries. Search for the affected user to get the right entry. The important part here is the Caller Machine Name. This name will tell you the server which is causing the bad logins. Another crucial detail is the value of the logon type. With this value you can localize the cause. The possible values are listed here:
https://docs.microsoft.com/en-us/windows/security/threat-protection/auditing/event-4625
Finally, it should be relatively easy to solve. The possible sources of the bad logins are for example:
- Scheduled tasks
- Services
- Stored credentials
- File share access
- …
Thus, you can check now the local client of the user in order to find the root cause, for example in Credential Manager and delete the stored credentials, re-map the network drive or adapt the scheduled task. Analyze User Lockout AD












